EXACT STEPS TO HACK CREDIT CARDS OR DEBIT CARDS
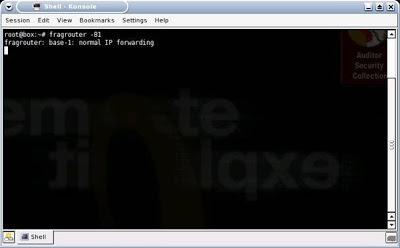
His first step would be to turn on Fragrouter, so that his machine can perform IP forwarding
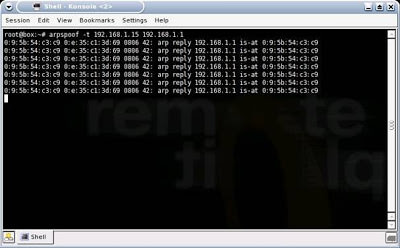
After that, he’ll want to direct your WiFi network traffic to his machine, rather than your data traffic going directly to the Internet. This enables him to be the “Man-in-the-Middle” between your machine and the internet. Using Arpspoof, a simple technique, he determines your IP address is 192.168.1.15 and the Default Gateway of the WiFi network is 192.168.1.1:
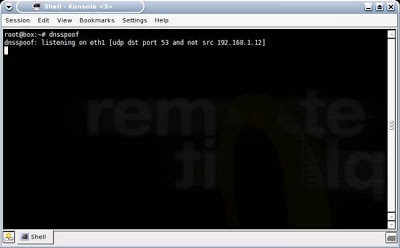
The next step is to enable DNS Spoofing via DNSSpoof:
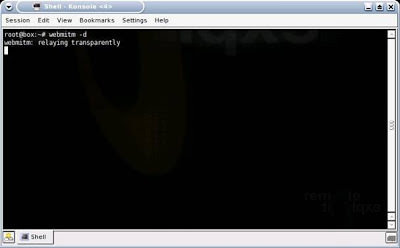
Since he will be replacing the bank or online store’s valid certificate with his own fake one, he will need to turn on the utility to enable his system to be the Man-in-the-Middle for web sessions and to handle certificates. This is done via webmitm:
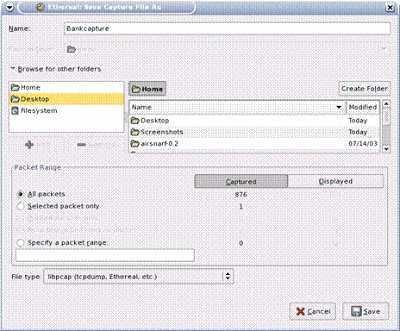
At this point, he is ready to go. Now he needs to begin actively sniffing your data passing through his machine, including your login and credit card information. He opts to do this with Ethereal, then saves his capture:
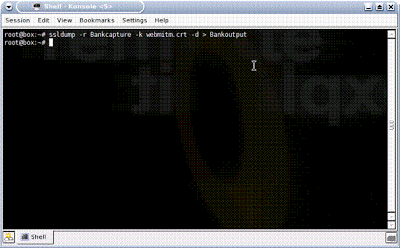
He now has the data, but it is still encrypted with 128-bit SSL. No problem, since he has the key. What he needs to do now is simply decrypt the data using the certificate that he gave you. He does this with SSL Dump:
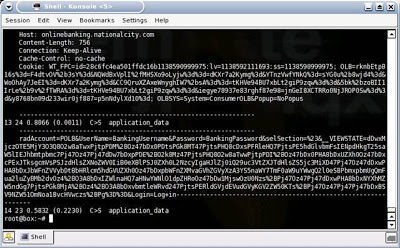
He runs a Cat command to view the now decrypted SSL information. Note that the username is “Bankusername” and the password is “BankPassword.” Conveniently, this dump also reveals the banking site as National City. FYI, the better, more secure banking and online store websites will have you first connect to another, preceding page via SSL, prior to connecting to the page where you enter sensitive information such as bank login credentials or credit card numbers. The reason for this is to stop the MITM-type attack. This helps because if you were to access this preceding page first with a “fake” certificate the next page where you were to enter the sensitive information would not display. The page gathering the sensitive information would be expecting a valid certificate, which it would not receive because of the Man-in-the-Middle. While some online banks and stores do implement this extra step/page for security reasons, the real flaw in this attack is the uneducated end-user, as you’ll soon see:
With this information, he can now log into your online bank account with the same access and privileges as you. He could transfer money, view account data, etc.
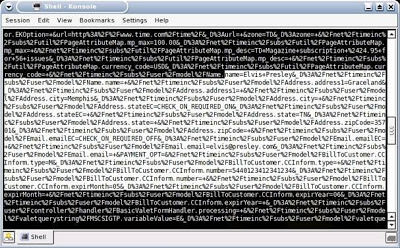
Below is an example of a sniffed SSL credit card purchase/transaction. You can see that Elvis Presley was attempting to make a purchase with his credit card 5440123412341234 with an expiration date of 5/06 and the billing address of Graceland in Memphis, TN (He is alive!). If this was your information, the hacker could easily make online purchases with your card.
Bad News for SSL VPN Admins
This type of attack could be particularly bad for corporations, because Corporate SSL VPN solutions are also vulnerable to this type of attack. Corporate SSL VPN solutions will often authenticate against Active Directory, the NT Domain, LDAP, or some other centralized credentials data store. Sniffing the SSL VPN login then gives an attacker valid credentials to the corporate network and other systems.
What an End-User Needs To Know
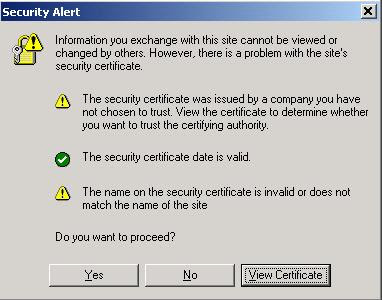
There’s a big step an end-user can take to prevent this from taking place. When the MITM Hacker uses the “bad” certificate instead of the “good,” valid certificate, the end-user is actually alerted to this. The problem is that most end-users don’t understand what this means and will unknowingly agree to use the fake certificate. Below is an example of the Security Alert an end-user would receive. Most uneducated end-users would simply click “Yes”… and this is the fatal flaw:
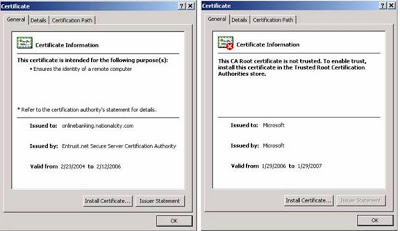
By clicking “Yes,” they have set themselves up to be hacked. By clicking the “View Certificate” button, the end-user would easily see that there is a problem. Below are examples of the various certificate views/tabs that show a good certificate compared to the bad certificate:
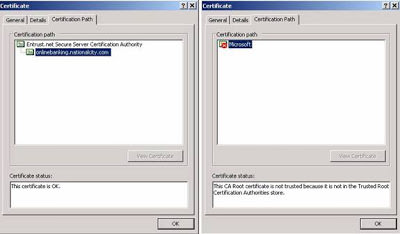 |
| Left One Good Certificate and right one fake certificate |
How an End-User Can Prevent This
- Again, the simple act of viewing the certificate and clicking “No” would have prevented this from happening.
- Education is the key for an end-user. If you see this message, take the time to view the certificate. As you can see from the examples above, you can tell when something doesn’t look right. If you can’t tell, err on the side of caution and call your online bank or the online store.
- Take the time to read and understand all security messages you receive. Don’t just randomly click yes out of convenience.
How a Corporation Can Prevent This
- Educate the end-user on the Security Alert and how to react to it.
- Utilize One Time Passwords, such as RSA Tokens, to prevent the reuse of sniffed credentials.
- When using SSL VPN, utilize mature products with advanced features, such as Juniper’s Secure Application Manager or Network Connect functionality.