You computer is likely to contain crucial information, maybe it's
personal or professional. It is necessary that you keep it safeguarded
from third party interruptions and data leakage. Most of us tend to
provide a screen login password through which the laptop remains safe
from the hands of unknown people trying to access it. This piece of
letters, number and special characters is of crucial importance. If in
case by trying to keep it extra safe you end up forgetting the password
yourself then it will be a mess of a situation to control because
without access to the password you cannot open the laptop. Considering
that a Windows 7 laptop at your disposal contains several important
details, you need to provide it with a password to maintain protection
and also not forget it yourself.
Two ways to help you regain acess to your Windows.
-
Method 1. Bypass Windows 7 Password with Command Prompt
-
Method 2: Bypass Administrator Password on Windows 7 with Recovery UtilityYou will be locked out of windows 10/8/7 once you
type the incorrect password, however it often happens that you lose
track of it because there are so many things on your mind. It would be
a major headache if you forgot Windows 10 , 8 or Windows 7 Administrator password.
Luckily, there are still always a few methods to bypass your Windows 7
or higher computer without system reinstallation and data loss, but
Some of these are time consuming or boring as you must walk through the
whole process, and some are a few simple.
In this artcile, we will show you two
ways to demonstrate how to bypass Windows 7 Administrator password when you're locked out of Windows, it also works fine with local account in Windows 8/8.1 and Windows 10.
Part 1: Bypass Windows 7/8/10 Password with Command Prompt
Command Prompt is an easy yet free way to reset your forgot Windows 7 Administrator password, but it's difficult and risky to perform Command Prompt especially for those who lack of technical knowledge.
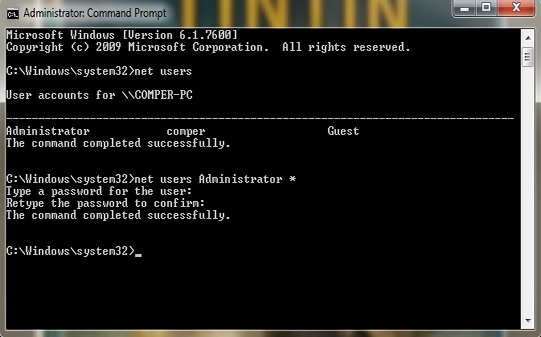
1) First you need to restart your computer
2) Then press F8 to enter "Safe Mode" then navigate to the "Advanced Boot Options".
3) There are 3 boot options for your choice, select the Safe Mode with Command Prompt.
4) Wait for a while, you can see Windows 7 boots up to the login screen. Choose administrator,
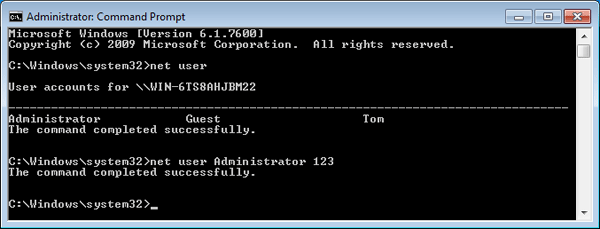
5) Go to Start > Run and type cmd.exe, a Command Prompt dialog box pops up.
6) Type net user and press Enter. All the windows accounts will be listed, then type the acount you wish to change.
7) when the command is completed successfully, the new password has been successfully reset.
Frankly speaking, When you're locked out of Windows,
I don't suggest you perform this method if you're not a tech guy, if
you persist in that, you may damage to your computer or lost system
data, all at your own risk. You might take a look at the Part 2 and then
determine which method is the best.
Part 2: Bypass Administrator Password on Windows 7/8/10 with Recovery Utility
To bypass the Windows 7 screen password, you might be told to try
pre-created password reset disk
to remove your password, but in most case, this is impossible because
the password reset disk must created before your forgot the password. If
you don't have a reset disk, maybe the Command Prompt works for you. Or
try professional but safe program - iSeePassword
Windows Password Recovery application to
bypass Windows 7 password
without system reinstallation. With it, you will be able to retrieve
the lost or forgotten Administrator password and grant your access to
your system, it provides two ways to create a booable reset disk with
USB drive or DVD, then safely and easily reset administrator and other
local user accounts for Widnows 7, 8/8.1 and Windows 10. The principle
of this program is very simple, it just writes a new ISO image files to
your flash drive or DVD to create a reset disk, never damage to your
original data and system.
-
Just 3 simple steps to reset forgotten Windows local administrator, domain and other user account passwords.
- Two ways to create bootable reset disk with CD/DVD or USB flash drive. No need to format or re-install Windows!
- Support various brands of desktops, laptops and tablet PCs, like Dell, Hp, Sony, Toshiba, Acer, Samsung and ThinkPad, etc.
- Support Windows 10, 8.1, 8, 7, Vista, XP, 2000, etc. and Windows server.
Support Windows OS : Windows 10/10.1/10.2, Windows 8/8.1 and Windows 7/Vista/XP
What You Need:
1) Prepare a blank DVD/CD or a USB flash drive with no less then 1G capacity.
2) An accessible Windows computer. You can borrow from your friend's if you haven't.
3) Password reset tool, directly download it below.
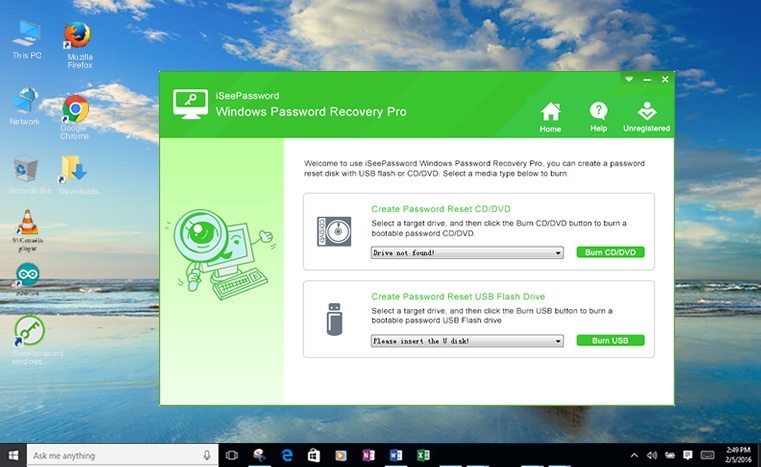
1Download and Install Windows Password Recovery on Your Another Normal Computer
First of all, you need to download and install program on another
accessible computer firstly, the installation is easy to operate, then
open the program. You will see the main Window below.
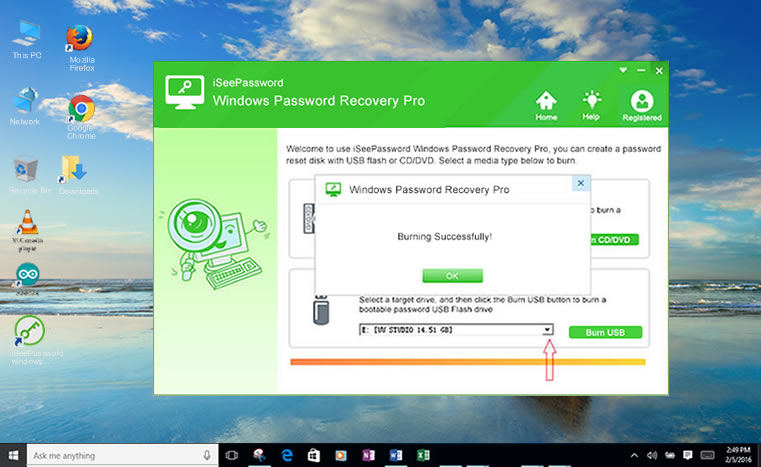
2Start to Make a Bootable Recovery Disk ( Here we take USB for example)
This program provides two ways to create a recovery disk (USB or
DVD/CD), here we take USB flash for example. After the installation,
insert your USB flash to a normal Windows computer, then you'll be asked
to select a Media type to create a recovery disk.
Here you should click the USB Device button and select your USB drive from the drop-down list. Then click "
Burn USB"
to let the program burn the ISO images files to your USB drive. It will
take some time to finish the burning process. Please be patient! Don't
disconnect your USB to your computer before the burning finishes.
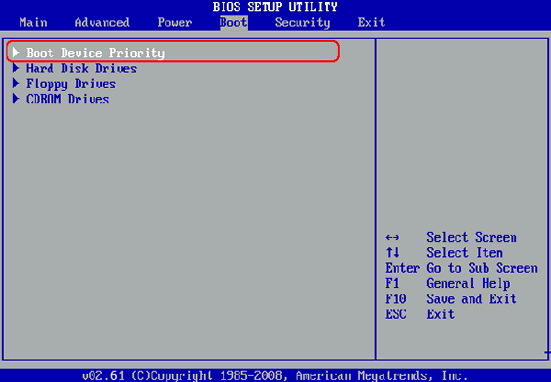
3Insert the USB Drive to Your Locked Computer and Boot Computer from USB
After created a recovery disk with your USB drive, then insert it
to your locked computer. Here it's also noteworthy that you must change
BIOS boot sequence to make it boot from USB. Restart your locked
computer and press "Del" or "F2" button while the computer is
initializing, then Go to the bios setting and change the BIOS options.
After all, press F10 to save your changes.
4Start to Reset Your Password, then Reboot Your Computer
Keep the USB dive plugged to your computer and reboot your computer after the boot order has been changed into USB. Then
Windows Password Recovery
program will be startup during the booting, you will see the main
screen. It will automatically detect all the current account and list to
you. Just select the target user that you want to reset. Then click the
"Reset Password" button.
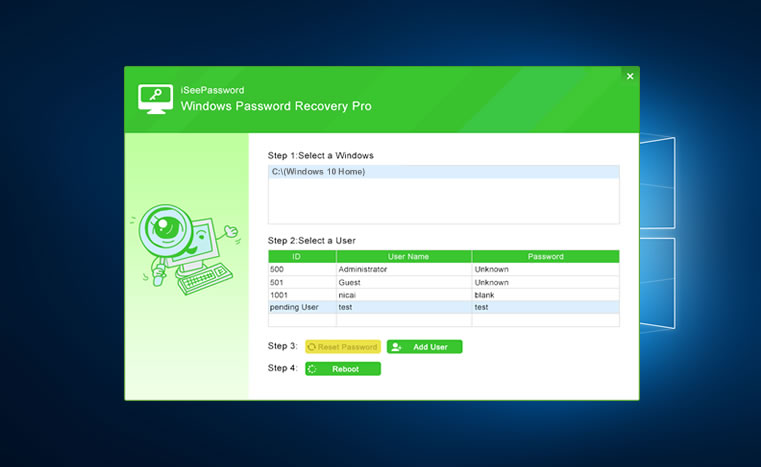
After the password reset, the password of the target user you
select will be blank. "Congratulation" message will pop up once the
password has been reset successfully. Then Click "Reboot" to restart
computer without login password.
There is one thing you can guarantee yourself of and that is
security. No amount of crucial data is going to be lost while the
software does its work. You can be sure that safety is the number one
priority here and you can absolutely rely on its system functions to
provide you the best of password recovery services. If you're
locked out of Windows 10,
8, Windows 7, Vista or XP, you can either use the professional,
personal or advanced version to suit your needs. It is flexible with
several application ranges that can be used successfully to gain the
best recovery benefits. Therefore you no longer will have to worry if
you
forgot the Windows password and need to get it fixed urgently without having to resort to monetary services.
There is no doubt that password protection on your Windows 7, 8 or
10 is very important to your files, without password, anyone who can get
physical access to your Windows and stole your files, photos or emails.
If you forgot it, you still have the chance to bypass Windows 7 login
password. This
iSeePassword Windows Recovery tool will guide you through the process that will be responsible in giving you back your password. Just do it by yourself.


















 Unfortunately,
the Disk Cleanup may not delete every file in the temp directory.
Therefore, we also suggest deleting temporary files manually. To do
this, open the Start Menu and type %temp% in the Search field. In Windows XP and prior, click the Run option in the Start Menu and enter %temp%
in the Run field. Press Enter and a Temp folder should open. You can
delete all files found in this folder and, if any files are in use and
cannot be deleted, they can be skipped.
Unfortunately,
the Disk Cleanup may not delete every file in the temp directory.
Therefore, we also suggest deleting temporary files manually. To do
this, open the Start Menu and type %temp% in the Search field. In Windows XP and prior, click the Run option in the Start Menu and enter %temp%
in the Run field. Press Enter and a Temp folder should open. You can
delete all files found in this folder and, if any files are in use and
cannot be deleted, they can be skipped.













