TECHNICAL ANALYSIS
The updated Craxs Remote Administration Tool now includes an additional build option. The primary build option is already available, offering a range of destructive features with a few new add-ons, however, the Android package in the primary build contains code similar to what was previously reported, i.e. the new add-on to the panel enables threat actors to create a dropper. When combined with well-planned social engineering, this feature can further ensnare Android users. In our further analysis, we delve into the dropper’s functionality and how the payload code serves as a dropper.
PROCESS OVERVIEW
The panel’s main builder enables the threat actor to configure the connection between the compromised device and command & control.
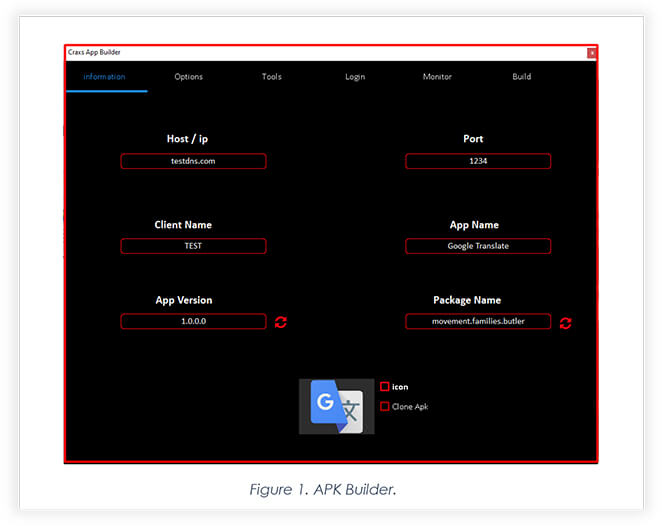
The panel also allows threat actors to customize the main payload by choosing icon, size, and website to add to the web view module.

Below snippet shows the destructive features the panel offers threat actors to inject into the main payload.
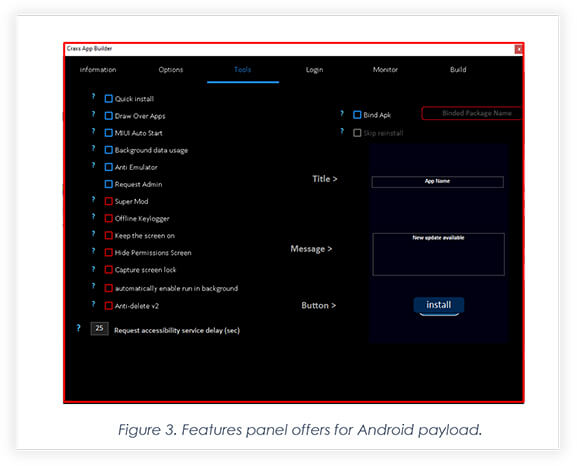
Threat actors can customize the credentials monitoring of any website they want to.

The final build page allows threat actors to choose permissions they want to exploit and then generate the main payload.

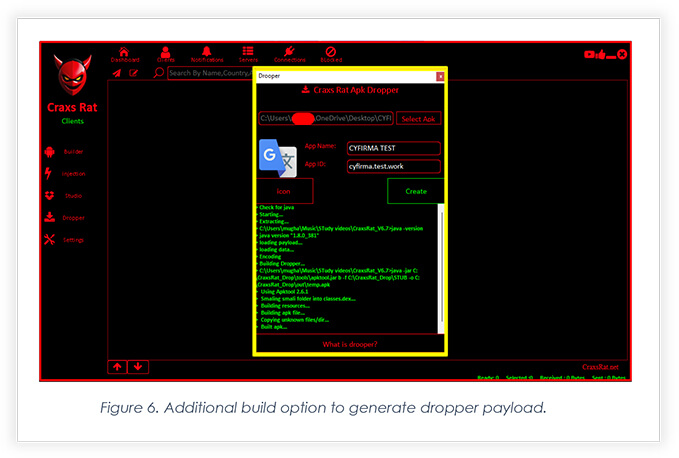
Figure 6 highlights a new add-on to the tool. This new build option allows threat actors to build an Android package that will help attackers to deliver the main payload to fully compromise the device.
When it is opened after installation, victims are taken to the page where the background dropper fetches the main payload. The user interface, meanwhile, displays ‘Downloading updates’ graphics.

Once the app is fetched in the background, the dropper app then asks the victim to click on the update button.
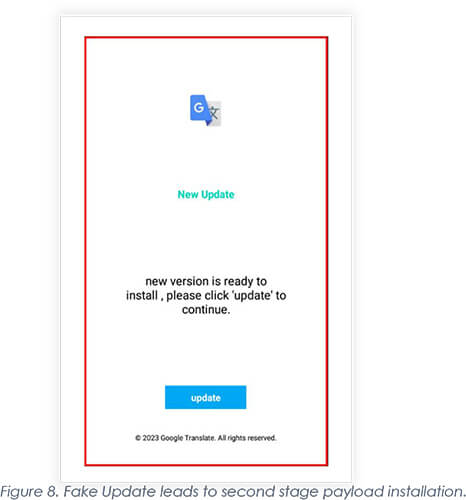
Upon clicking ‘update’ (Figure 8), the apps take victims to the next page where they interact with the main payload for its installation.

Once installed, the victim is asked to enable accessibility to exploit the permissions and fully compromise the android devices.

We have the latest version of CraxsRat with lifetime license. visit our newly created telegram channel to purchase direct from us




